Access Entry
It is possible to configure Vaticy to connect to your Kubernetes cluster with an Access Entry.
EKS clusters can be configured to have an Access Entry that allows specific IAM roles or users to access the cluster.
The IAM roles and users are attached to specific policies or RBAC groups within the cluster.
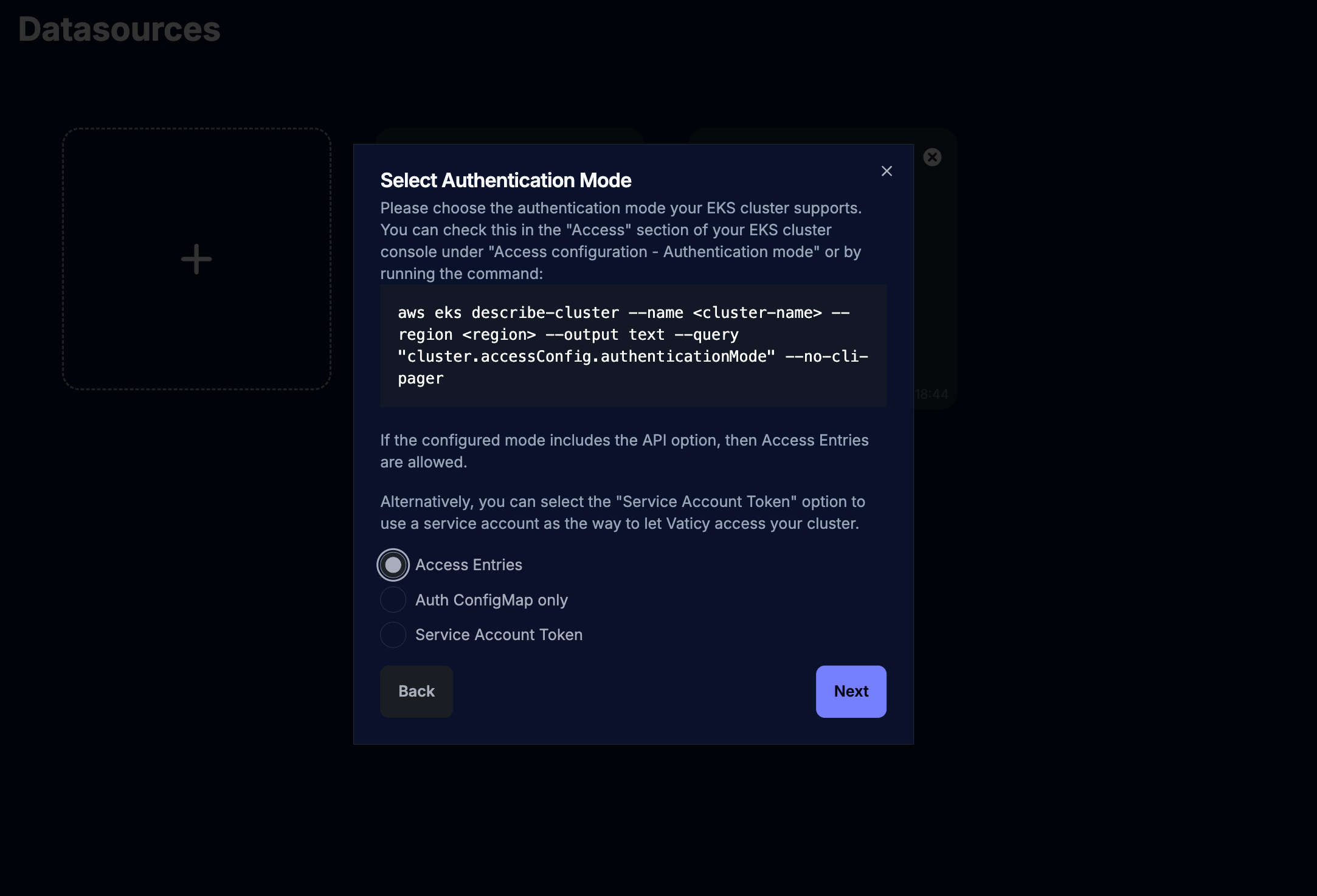
Permissions for accessing the EKS cluster
An EKS cluster has to be configured to allow using access entries as a way to authenticate to the cluster.
This configuration can be viewed in the Access tab in your EKS cluster console,
or when running the following command using your cluster name and region and an authenticated AWS CLI profile:
aws eks describe-cluster --name <cluster-name> \
--region <region> \
--output text \
--query "cluster.accessConfig.authenticationMode" \
--no-cli-pager
The output can be,
for example,
API_AND_CONFIG_MAP,
which means that the cluster is configured to allow both Access Entries and the Auth ConfigMap.
If Access Entries are used,
Vaticy's agentless collector CloudFormation stack creates an Access Entry,
in addition to the IAM role and IAM policy,
to the specified cluster.
The access entry is created with access policy of AmazonEKSAdminViewPolicy which allows the agentless collector to only view the resources in the cluster.
The available access policies can be found in the EKS documentation.
This policy can be changed to a more restrictive policy if needed or to use a custom RBAC group bound to a custom ClusterRole.
Connecting Vaticy to the EKS cluster
Start by choosing the Access Entries option:
Now please follow the general instructions about Creating a CloudFormation Stack. Continue from here when you are done.
Note: Deleting the
IAMwill makeVaticylose the ability to communicate with the cluster.
To finish the configuration,
click on Create and the EKS agentless collector will be deployed.
Now please read the Status page to check the status of the new deployed agentless collector.