Overview
The EKS agentless collector is a Kubernetes collector that is used to view EKS clusters resources.
The EKS agentless collector is deployed on our end and it is configured to access the EKS cluster using the IAM role created.
Once deployed the EKS agentless collector will start to gather your cluster resources templates and look for issues and changes that could lead to the issues.
Configuration
There are 3 ways to allow Vaticy to integrate with your cluster:
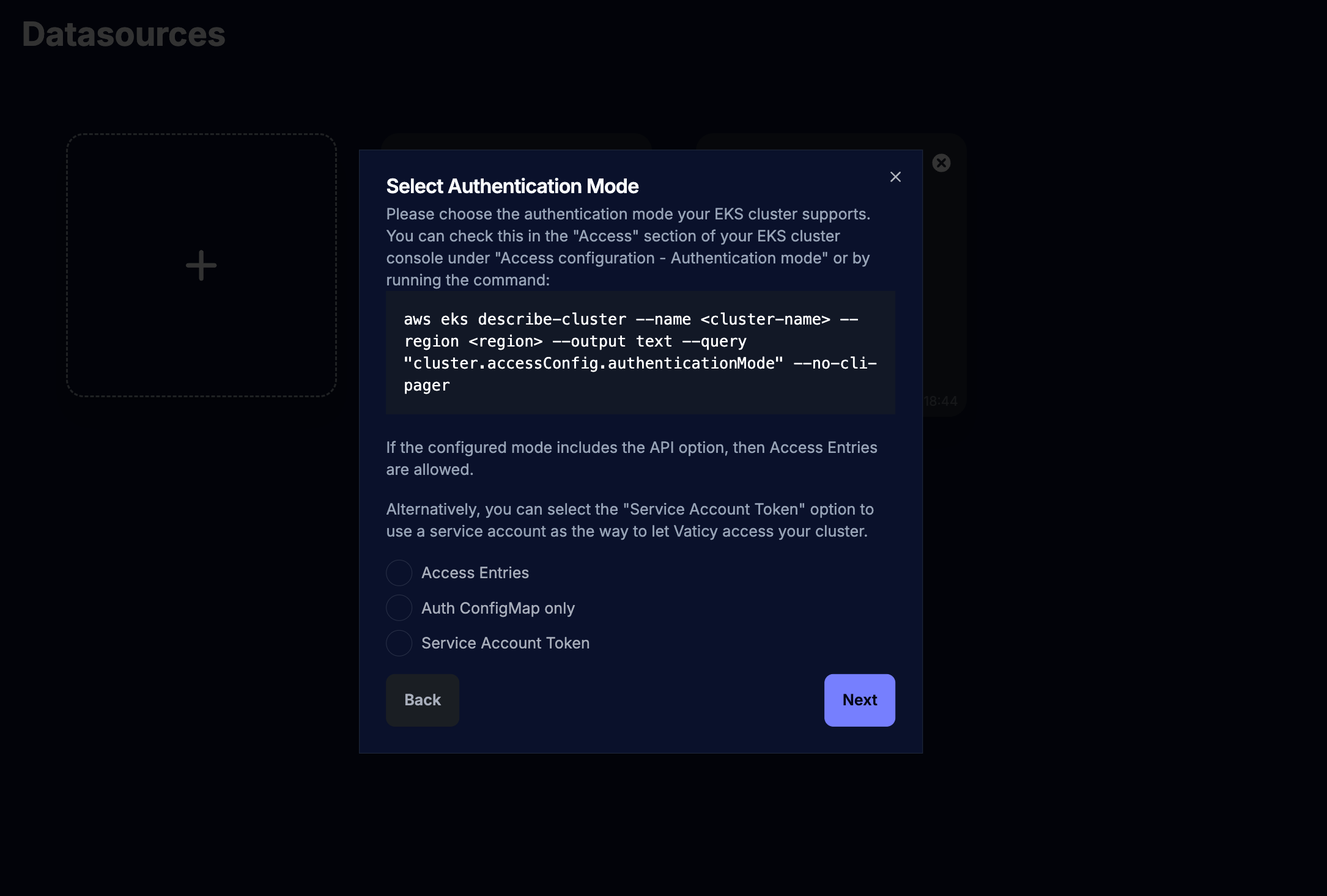
- Create an
Access Entry - Create only an
Auth ConfigMap - Create a
tokento a newService Account
In the Datasources page, press the + button and select the EKS option.
Configure the EKS details:
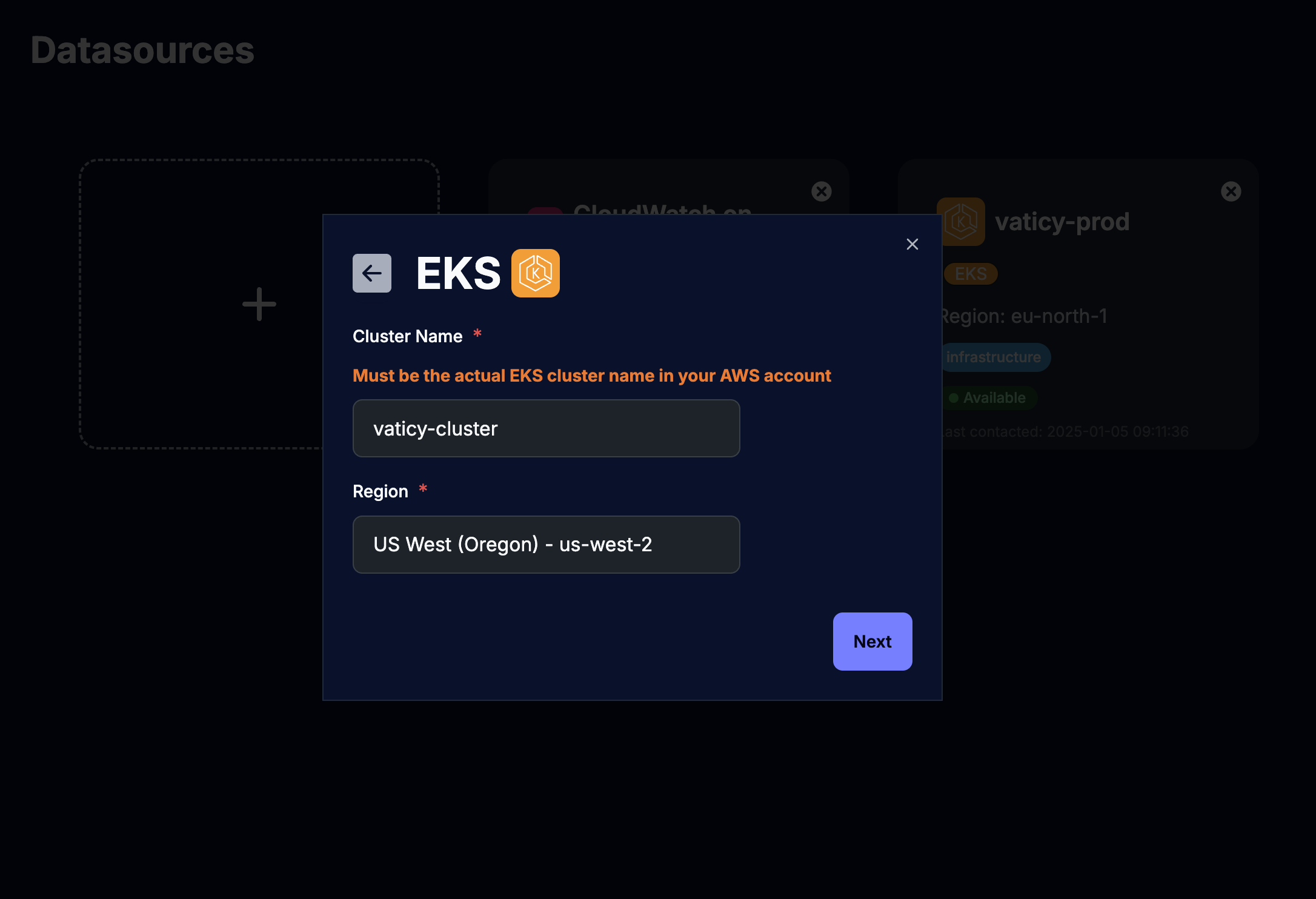
Note: The cluster name should be the name of the
EKScluster as it is configured in yourAWSaccount.
After clicking Next you should see a dialog explaining about the different authentication modes.
The 3 methods are described in the following pages:
General Permissions
The following IAM Role paragraph is valid for each one of the three possible configurations:
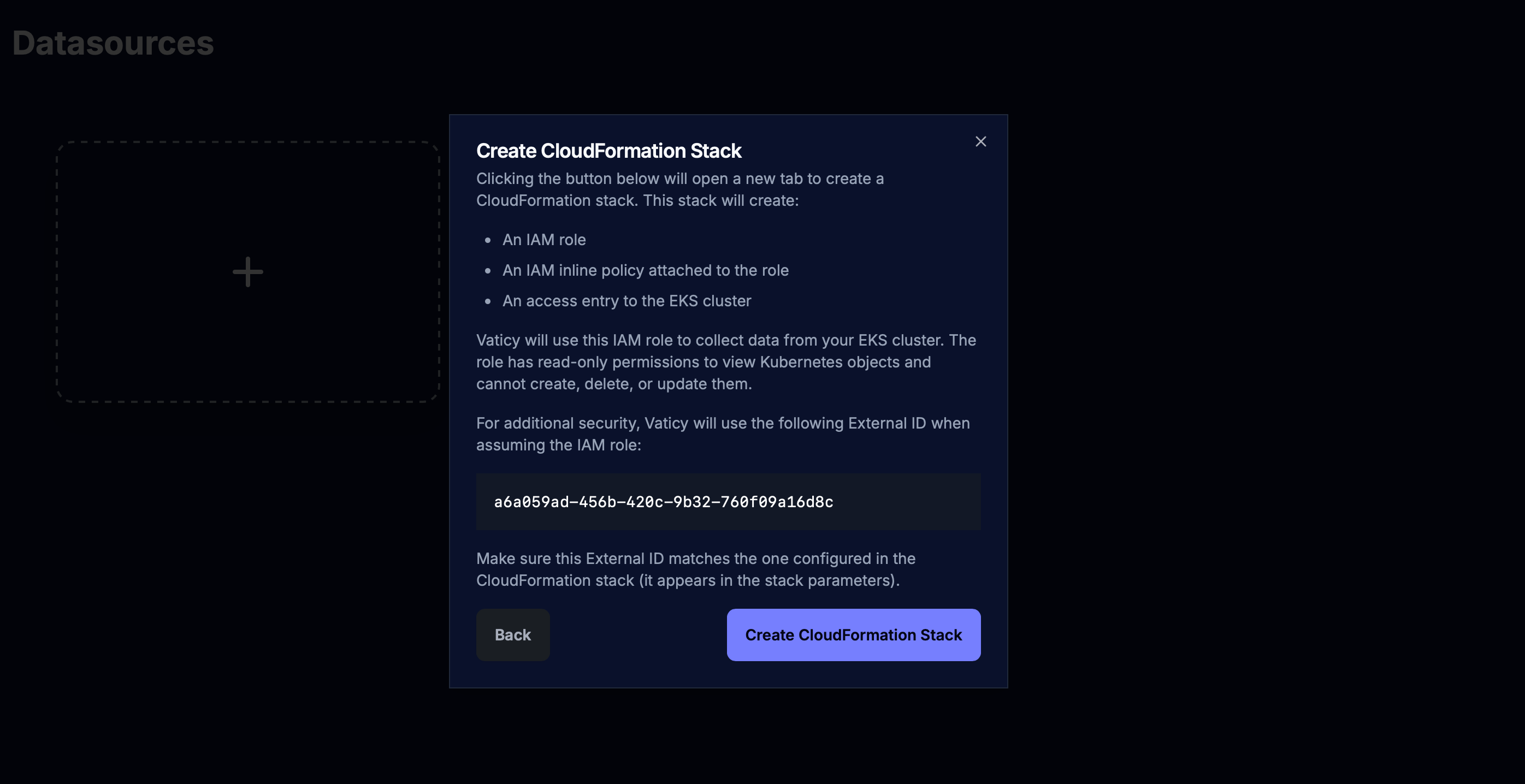
The CloudFormation stack creates an IAM role for the agentless collector to use when accessing the EKS cluster.
The IAM role is created with the a policy attached with the eks:DescribeCluster permissions.
The role is created with a trust relationship that allows only our vaticy-cluster-watcher user to assume the role using the configured external ID - a UID generated when connecting the EKS datasource,
that the vaticy-cluster-watcher user has to provide when assuming the role.
CloudFormation Stack
After clicking Next you should see a dialog explaining what AWS resources will be created in the CloudFormation stack.
Clicking on Create CloudFormation stack will open in a new tab your AWS console where you will have to confirm the creation of the stack:
You can also verify the generated UID in the Vaticy dialog matches the one used as parameter in the AWS CloudFormation console.
Make sure to acknowledge the creation of the stack and click on Create stack in the AWS console:
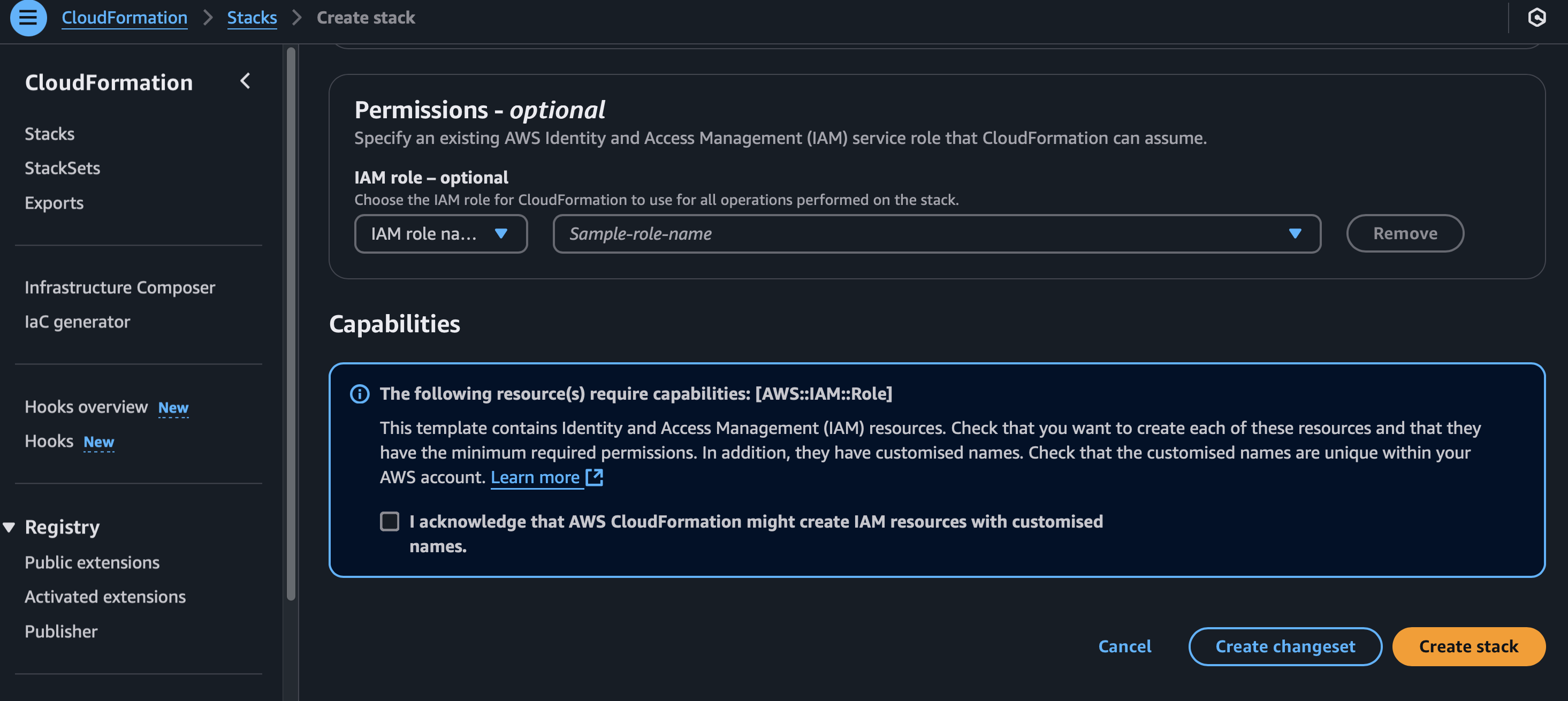
After the stack is successfully created,
you will have to copy the created IAM role ARN and paste it back in the last step of the configuration in Vaticy.
You can find it in the CloudFormation stack outputs or in the link provided in the Vaticy dialog which opens the IAM management console in the role that should have been created:
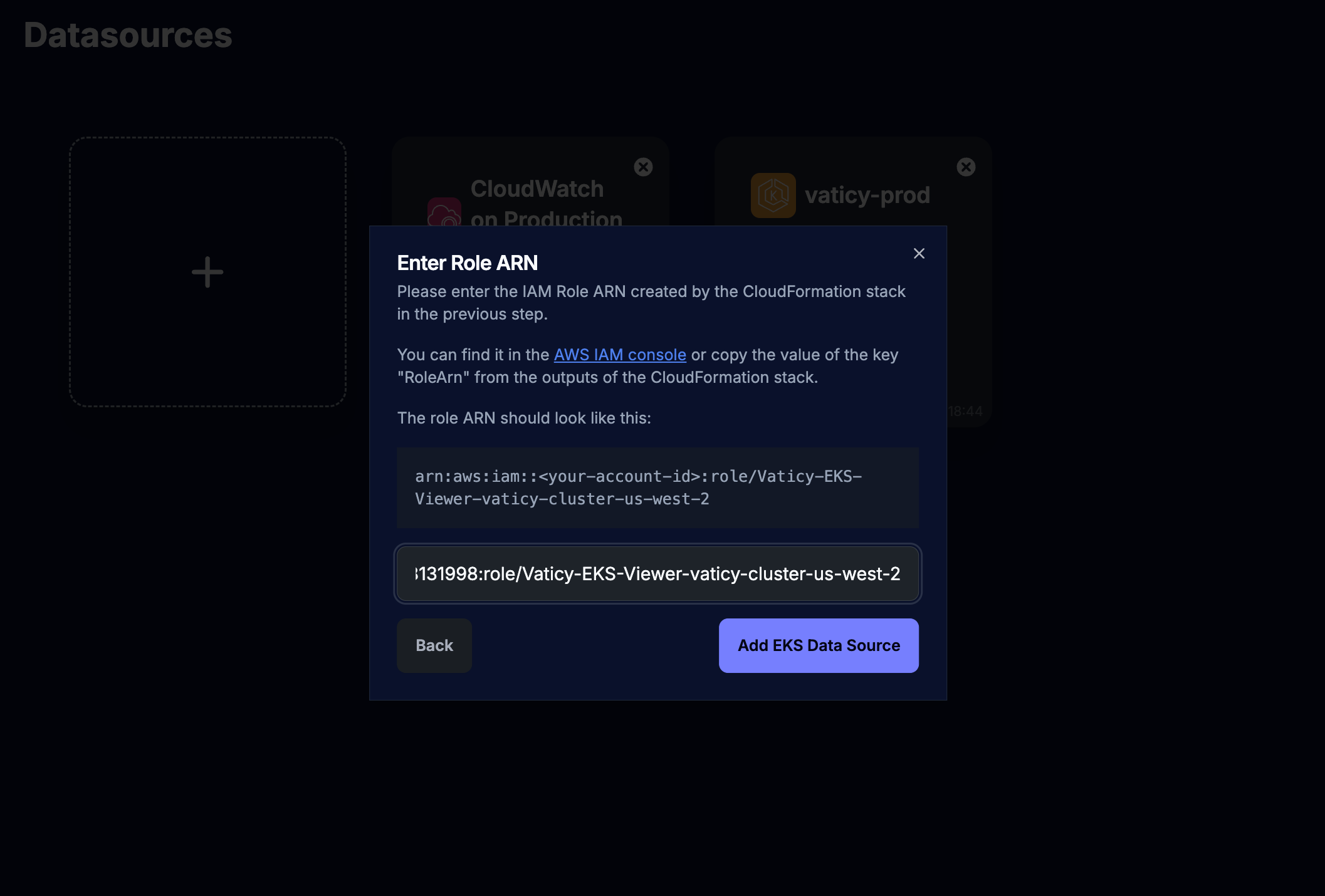
Pressing on the Add EKS Data Source will transfer you to a unique dialog which depends on the previously chosen configuration type.
Please read each specific configuration docs for more information about the dialog.